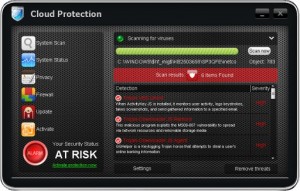
Cloud Protection is a rogue of the FakeScanti Family, which uses scare tactics, fake scan results of the computer being infected, and the blocking of other applications when trying to run them to goad the user into buying the rogue to clean the fake infections shown. Files and Locations: %SYSTEM%\<Random Named File>.exe %AppData%\svhostu.exe The Cloud …
Oct 10
System Restore Rogue of the FakeSysDef Family
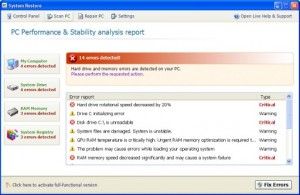
System Restore, a rogue of the FakeSysDef Family which uses fake scareware tactics of having hard drive and system errors to scare those infected to purchase the rogue. The System Restore rogue may also includes an MBR (Master Boot Record) Rootkit like TDL4, or Sinowal used for profiting from search engine results hijackings even after the user purchases the rogue. Files and Locations: %LOCAL_APPDATA%\<Random File …
Oct 10
Guard Online Rogue of the FakeScanti Family
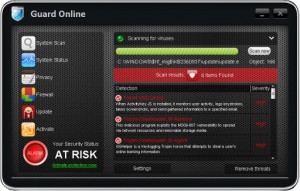
Guard Online is a rogue of the FakeScanti Family, that uses scare tactics and fake scan results showing the computer is infected along with the blocking of all other applications when trying to run them to scare the user into buying the rogue to clean the fake scan results shown. Files and Locations: %SYSTEM%\<Random Named File>.exe …
Oct 07
AV Guard Online Rogue of the FakeScanti Family
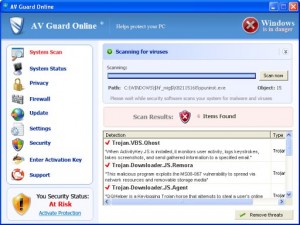
AV Guard Online is a rogue of the FakeScanti Family, that uses fake alert scare tactics and fake scan results showing the computer is infected tactics along with the blocking of other applications when trying to run them to scare the user into purchasing the rogue to clean the fake scan results it shows. This …
Oct 05
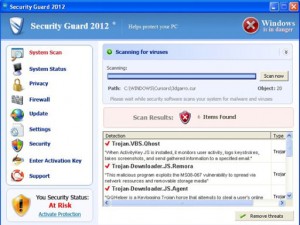
Security Guard 2012 Rogue of the FakeScanti Family
Security Guard 2012 is a rogue of the FakeScanti Family, that uses fake alert scare tactics and fake scan results showing the computer is infected tactics along with the blocking of other applications when trying to run them to scare the user into purchasing the rogue to clean the fake scan results it shows. This …
Oct 04
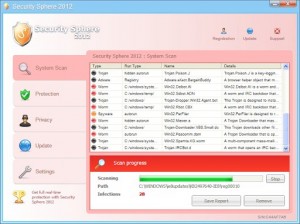
Security Sphere 2012 Rogue of the WinWeb Security Family
Security Sphere 2012 Rogue of the WinWeb Security Family replaces the Personal Shield Pro clone. This rogue like so many of today’s rogues, block the the running of all other applications and the constant pop ups and re-directs to scare messages designed to scare those infected into purchasing the rogue. Files and Locations: %COMMON_APPDATA%\<random named> .exe …
Sep 30
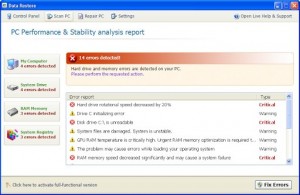
Data Restore rogue of the FakeSysDef Family
Data Restore, a rogue of the FakeSysDef Family which uses fake scareware of having hard drive and system errors to scare those infected to buy the rogue. The FakeSysDef rogues also includes an MBR (Master Boot Record) Rootkit like TDSS, TDL#, or Sinowal used for profiting from search engine results hijackings even after the user purchases the rogue. Files and Locations: %LOCAL_APPDATA%\<Random File …
Sep 29
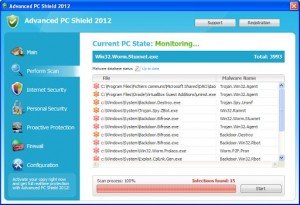
Advanced PC Shield 2012 Rogue
The Advanced PC Shield 2012 rogue is only one file, however, it also includes a Necurs.c rootkit. This rogue doesny’lock the running of other applications but it can hijack the browser re-directing to scare messages to try and get the user to purchase the rogue. While the rogue is running at one point it begins …
Sep 22
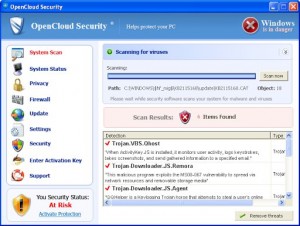
OpenCloud Security Rogue of the FakeScanti Family
OpenCloud Security is a rogue of the FakeScanti Family, that uses fake alert scare tactics and fake scan results showing the computer is infected tactics along with the blocking of other applications when trying to run themtogoad the user into purchasing the rogue to clean the fake scan results it shows. Files and Locations: …
Sep 14
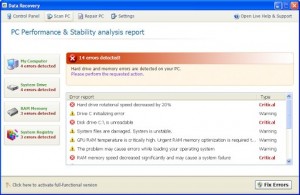
Data Recovery rogue of the FakeSysDef Family
Data Recovery is a rogue of the FakeSysDef Family and uses fake analysis generating scareware fake alerts of having hard drive and system errors to scare those infected to buy the rogue. These FakeSysDef rogues includes an MBR (Master Boot Record) Rootkit like TDSS, TDL#, or Sinowal created to profit from search engine results hijackings …