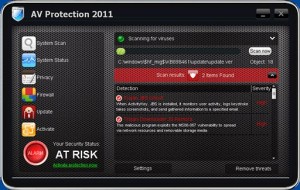
AV Protection 2011 is a rogue of the FakeScanti Family, that uses deceptive tactics, fake spam email alerts, and results of fake scans showing the computer being infected, and also the blocking of all applications when trying to run them to scare the user into buying the rogue to clean the fake infections shown. Files …
Category: Rogue Antispyware
Nov 15
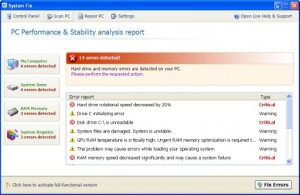
System Fix Rogue of the FakesysDef Family
System Fix, a rogue of the FakeSysDef Family which uses fake scareware of having hard drive and system errors to scare those infected to buy the rogue. The FakeSysDef rogues also includes an MBR (Master Boot Record) Rootkit like TDSS, TDL#, or Sinowal used for profiting from search engine results hijackings even after the user purchases the rogue. Files and Locations: …
Nov 10
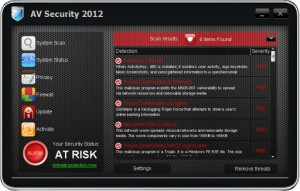
AV Security 2012 Rogue of the FakeScanti Family
AV Security 2012 is a rogue of the FakeScanti Family, that uses scare tactics with fake scans results, fake Blue Screens with a fake windows restarting screen, along with the blocking of all applications when trying to run them to goad the user into buying the rogue to clean the fake infections shown. This new …
Nov 06
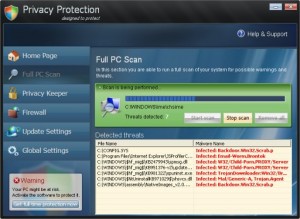
Privacy Protection Rogue of the Malware Protection Family
Privacy Protection is a rogue that is part of the Malware Protection family of rogues that uses fake alert and fake scan results as scare tactics to get the user to purchase the rogue. Files and Locations: %COMMON_APPDATA%\privacy.exe When the rogue runs, it blocks the running of all other applications, except when in Safe Mode, one …
Oct 23
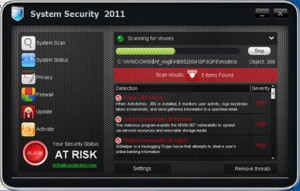
System Security 2011 Rogue of the FakeScanti family
System Security 2011 is a rogue of the FakeScanti Family, that uses scare tactics, fake scan results showing the computer is infected, and the blocking of all applications when trying to run them to scare the user into buying the rogue to clean the fake infections shown. Files and Locations: %SYSTEM%\<Random Named File>.exe %AppData%\svhostu.exe The …
Oct 19
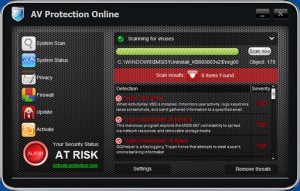
AV Protection Online Rogue of the FakeScanti Family
AV Protection Online is a rogue of the FakeScanti Family, that uses deceptive tactics, results of fake scans showing the computer being infected, along with the blocking of all applications when trying to run them to goad the user into buying the rogue to clean the fake infections shown. Files and Locations: %SYSTEM%\<Random Named File>.exe …
Oct 11
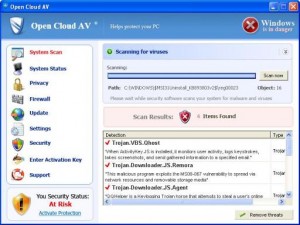
Open Cloud AV Rogue of the FakeScanti Family
Open Cloud AV is a rogue of the FakeScanti Family, that uses scareware tactics, fake scan results of the computer being infected, and the blocking of other applications when trying to run them to goad the user into buying the rogue to clean the fake infections shown. Files and Locations: %SYSTEM%\<Random Named File>.exe %AppData%\svhostu.exe The …
Oct 11
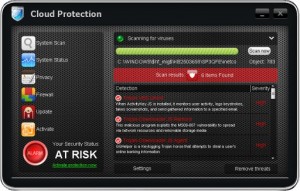
Cloud Protection Rogue of the FakeScanti Family
Cloud Protection is a rogue of the FakeScanti Family, which uses scare tactics, fake scan results of the computer being infected, and the blocking of other applications when trying to run them to goad the user into buying the rogue to clean the fake infections shown. Files and Locations: %SYSTEM%\<Random Named File>.exe %AppData%\svhostu.exe The Cloud …
Oct 10
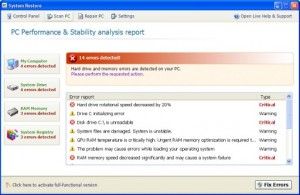
System Restore Rogue of the FakeSysDef Family
System Restore, a rogue of the FakeSysDef Family which uses fake scareware tactics of having hard drive and system errors to scare those infected to purchase the rogue. The System Restore rogue may also includes an MBR (Master Boot Record) Rootkit like TDL4, or Sinowal used for profiting from search engine results hijackings even after the user purchases the rogue. Files and Locations: %LOCAL_APPDATA%\<Random File …
Oct 10
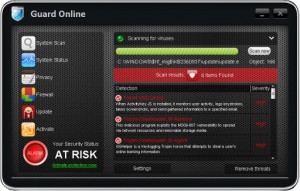
Guard Online Rogue of the FakeScanti Family
Guard Online is a rogue of the FakeScanti Family, that uses scare tactics and fake scan results showing the computer is infected along with the blocking of all other applications when trying to run them to scare the user into buying the rogue to clean the fake scan results shown. Files and Locations: %SYSTEM%\<Random Named File>.exe …