The impact caused by CryptoWall virus, which encrypts one’s data and holds it hostage while extorting a ransom, can be reversed using these instructions.
The malicious software to be dissected in this entry was once believed to have gone extinct, but the disappointment and fuss about it came back as its version 3.0 emerged back in January this year. CryptoWall is a highly persistent and extraordinarily belligerent sample of ransomware that impudently captures its victim’s files by means of encrypting them. This isn’t just a meaningless prank, however, as the virus goes ahead and extorts a fee afterwards in exchange for the personal information. The fact that the cybercriminal gang in charge of this campaign has been on the loose for a crazy long period of time is partly explained by the smart anonymization methods being applied. In particular, the communication with their servers is established through Tor gateways, which makes it really problematic to track the ill-minded guys down. In addition to this, the attacked users are supposed to pay in Bitcoins rather than via credit cards.
The principle used in this hoax isn’t new. The infection proper is brought to computers by dint of social engineering as well as exploits that use vulnerability-based security holes in systems. Contagious email attachments reportedly comprise the prevalent vector of these attacks, where users are lured into opening files in messages that look intriguing. Whereas this workflow can be avoided, exploit kits are much stealthier because the respective compromise is nearly impossible to notice, and antiviruses aren’t always capable of recognizing the bad signature.
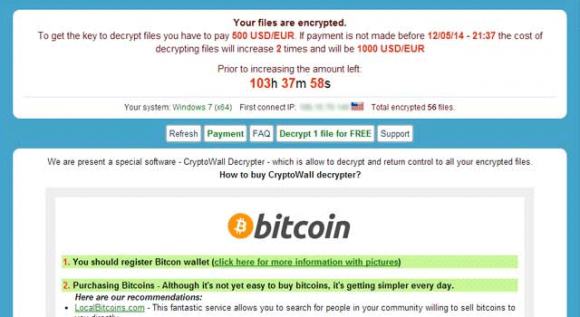
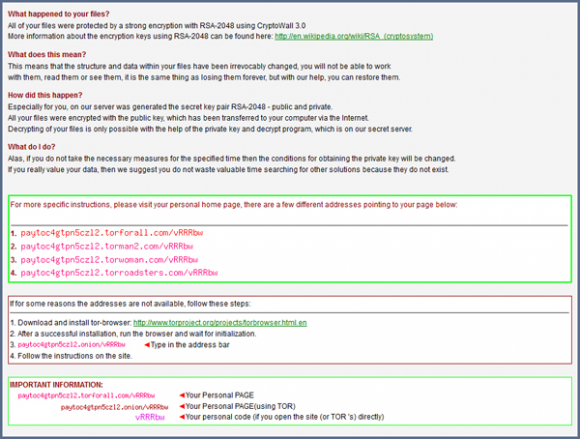
The kickoff of CryptoWall’s activity inside the infected workstation is accompanied by an inconspicuous scan of the hard disk, which pursues the goal of finding the user’s personal files based on the criterion of specific extensions, such as .jpg, .doc, .xls, etc. Every file that meets these hallmarks will be instantly encrypted with RSA-2048, a public-key cryptosystem that’s strong enough to be applied by governments. The chunks of data required for the decryption are stored outside of the target computer, so the recovery of files isn’t realistic without those keys. The so-called “CryptoWall decrypter”, therefore, is the service that the fraudsters try to sell to their victims for 500 USD. As it has been mentioned, this amount must be paid in Bitcoins. The deadline to submit the money is 7 days, or 168 hours. After this period expires, the ransom is going to increase 2 times.
The instructions regarding ransom payment are all enclosed in a file titled HELP_DECRYPT. Different variants of this file (HTML, PNG, TXT and URL) are dropped into all folders with encrypted items. The HELP_DECRYPT popups are encountered as soon as the user logs into Windows, providing hyperlinks to one’s “personal page” as well as the personal code to proceed.
No one has thus far come up with a method to restore CryptoWall encrypted files beyond submitting the ransom. The harm from the previous variant of this virus was somewhat easier to bypass, because it had deleted the user’s original files in a not-so-secure way, that is, via the native erase feature in Windows. In the meantime, encryption was applied to copies of the data rather than the files themselves. The latest version, CryptoWall 3.0, tends to wipe the information more securely, therefore automatic recovery utilities aren’t very likely to help. If you have gotten attacked by this infection, read the details below to learn what your file restore chances are. Again, there is no universal cure, but a couple of approaches might be useful.
CryptoWall virus automatic removal
It’s an odd thing but the CryptoWall program itself is not too persistent as far as removal is concerned. Reliable security software does the cleanup job, but be advised this is in no way related to restoring the encrypted data, which is an issue to be touched upon in the next part of this article. So, before you proceed with file restoration, it’s recommended to get rid of the ransomware proper so that it won’t cause you further trouble.
- Download and install the featured security tool and launch an in-depth malware checkup by clicking Start Computer Scan buttonDownload CryptoWall remover
- When the software returns a list of malicious and potentially unsafe items found on the PC, select Fix Threats in order to have the CryptoWall infection uninstalled from your machine. An additional virtue of this process is the elimination of other threats that may be active in the background.
Ways to retrieve personal files encrypted by CryptoWall
Method 1: Backups
Despite the fact that the share of users who regularly back up their data to the cloud or external storage is negligible, they are immune to malware attacks like this. So, if you are lucky enough to be one of these people, use backups to recover your personal information. Before doing so, make sure CryptoWall has been removed from the system (see previous section).
Method 2: Data recovery software
According to the recent research, this ransomware encrypts copies of files it detected on a computer. The original documents, photos etc. get erased. This is where you can benefit from file recovery tools which are designed specifically to find and restore objects that were previously removed from a PC. Even though CryptoWall deletes the original files with a number of overwrite passes, utilities like ParetoLogic Data Recovery Pro might address this problem.
Download data recovery software
Method 3: Shadow Volume Copies
There is a feature that Microsoft Windows is shipped with – it’s called Shadow Volume Copies. It means that all files on the computer are automatically subject to copying and storing. Be advised this only applies to the cases where the System Restore feature is turned on; luckily, that’s not a rare scenario. While the newest build of CryptoWall has some built-in countermeasures for recovering Shadow Volume Copies in the regular way, it’s strongly advised to give this method a try. It can be done manually or through the aid of a dedicated automatic tool.
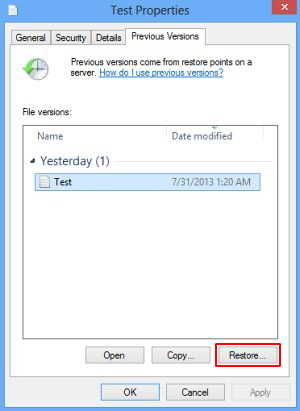
- Recover previous versions of filesPrevious versions are copies of files and folders that are automatically saved by the operating system when a restore point is created. Hopefully changes to your most critical files were made before the latest system restore point – in this case the information in them is going to be accurate for your needs. So do not fail to try this workaround. What you need to do is right-click on a file or folder of interest, select Properties and hit the Previous Versions tab. Then click Restore if you want to file recovered to its previous location, or hit Copy to restore it to a new place.
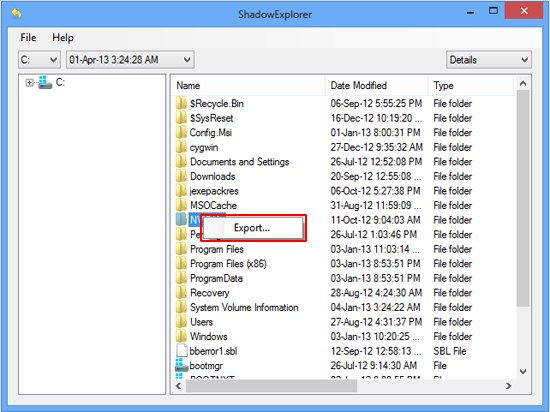
- Use the Shadow Explorer utilityRestoring files and folders can as well be performed automatically. For this purpose, tools like Shadow Explorer can be used. It provides you with all necessary controls and options to restore Shadow Volume Copies within one interface. Just right-click on the file or folder whose copies are to be restored, select Export, and follow the prompts.
Complete the CryptoWall virus removal process
Given the possible tenacity of this ransomware, it’s recommended to repeatedly check the machine for its components after the cleanup procedure has been performed. Now that you have hopefully managed to recover your most important personal files, rescan your system with trusted security suite to make sure CryptoWall extermination has been successful.
Download CryptoWall free scanner and remover


2 comments
My computer infected by cryptrowall 3.0 and all data photo, word document are locked . how can I recover my photo and word doc .
Author
Mahbub, the workflow provided in this guide should help you recover some files and eradicate the ransomware proper. Be sure to follow the instructions.