All the must-know details about TermBlazer Ads malware are at your fingertips in this post, including actionable virus prevention and removal recommendations.
The WYSIWYG (“what you see is what you get”) principle does not work for the applet called TermBlazer. The reason is about a tangible discrepancy between the officially proclaimed mission of this program and the features that come to light once a customer starts using it. Some of the operational markers of said application are pointing at obvious signs of adware traits. In fact, a little more in-depth dissection reveals its affiliation with such specimens of potentially unwanted software as WordFly and Infonaut – even their official websites’ design and layout are close to identical.
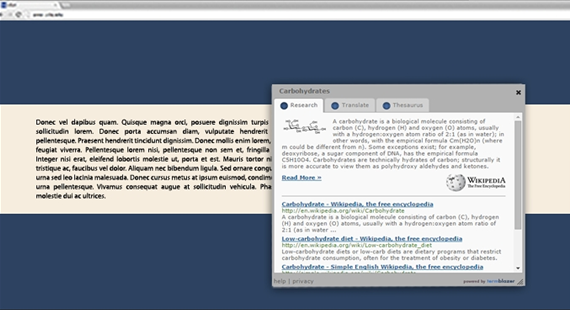
So, the vendor states upfront that TermBlazer is a free tool intended to return a number of lookup results right inside the web page that the user is currently on. These chunks of data supposedly include Bing and Wikipedia results for text that gets highlighted, and the output is claimed to appear in an in-page window. That’s a fairly convenient functionality to have at hand, but the whole usefulness fades away against the background of some serious caveats.
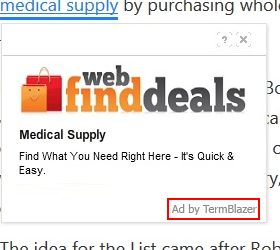
The utility in question is ad-supported, and the developer doesn’t really conceal this proviso. Therefore, whereas users should be prepared for possible advertising generated during their Internet sessions, they still get astonished at the volume of the sponsored information at the end of the day. Ubiquitous adverts, which are recognizable by the signatures reading “Ad by TermBlazer” or “TermBlazer Ads”, will inundate all visited sites. Some of these are banners and comparison shopping graphics; others are in-text ads that render multiple key phrases clickable and expand to pop-ups or pop-unders. Also, the victim might face a problem of interstitial pages going off whenever random space on a website is clicked.
One more reason why this app is a nuisance has to do with its furtive distribution. Instead of acquiring clients through transparent marketing and ethical search engine optimization techniques, the makers of TermBlazer choose adverse methodology to help their code land on PCs. Tight cooperation with freeware developers makes those ill-minded people’s day, because it’s via clumping with third-party software that the adware payload can safely trespass on virtually any machine. Media players and file downloaders with low to no reputation at all, as well as unofficial versions of Java or Flash Player – these are the main disseminators of the infection.
It’s quite a challenging task to get rid of TermBlazer once it is installed. Removing the pest is a matter of applying some out-of-the-common methods, the most effective one being provided in the follow-up chapters of the present article.
TermBlazer Ads virus automatic removal
All the other adware uninstall methods being worth a try, the cleanup using automatic security software guarantees a proven fix involving little user effort and a trouble-free procedure.
- Download and install the featured security tool and launch an in-depth malware checkup by clicking Start Computer Scan buttonDownload TermBlazer Ads remover
- When the software returns a list of malicious and potentially unsafe items found on the PC, select Fix Threats in order to have the TermBlazer infection uninstalled from your machine. An additional virtue of this process is the elimination of other threats that may be active in the background.
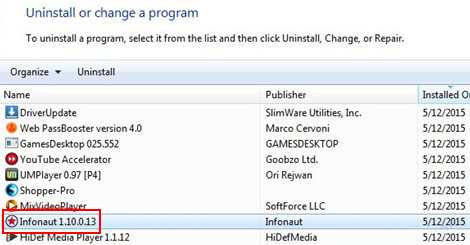
Use Control Panel to uninstall TermBlazer adware
- Go to Control Panel from Windows Start menu. If you are using Windows XP or Windows 8, proceed to Add or Remove Programs. If it’s Windows Vista or Windows 7, Uninstall a program is the right option to click
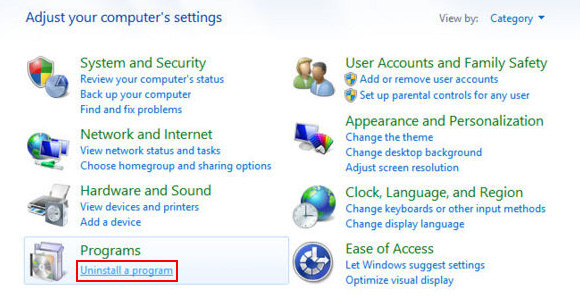
- Carefully examine the list and find the entry for TermBlazer or other suspicious programs there. Once spotted, select the Uninstall/Change option for this item in order to complete the removal
Reset the compromised browser to its defaults
Despite the fact that this is a fairly radical fix, resetting the affected web browser is effective. However, be advised you will lose your personalized settings such as temporary Internet files, history, cookies, saved passwords, web form data, toolbars and add-ons. So proceed with caution, and if you’re not sure – perform the cleanup using methods highlighted in the previous sections.
Reset Firefox to its original defaults
- Open Firefox, expand the Help menu on the top of the window, and in the drop-down list pick Troubleshooting Information. Alternatively, simply type in ‘about:support‘ (without quotes) in the Firefox omnibox and hit Enter.
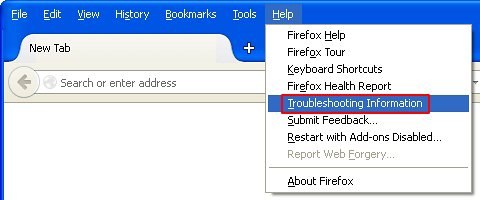
- Troubleshooting Information will open in a separate tab. Click the Reset Firefox button as shown. You’re now done.
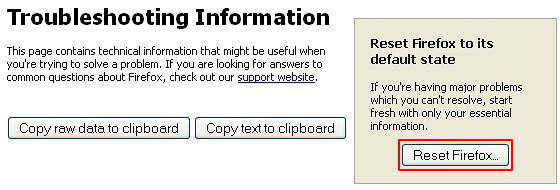
Reset Internet Explorer to its original defaults
- Launch Internet Explorer and proceed to Tools/Gear icon – Internet Options.
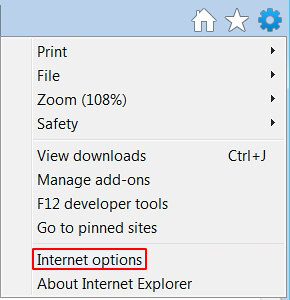
- Select the Advanced tab at the top and click Reset.
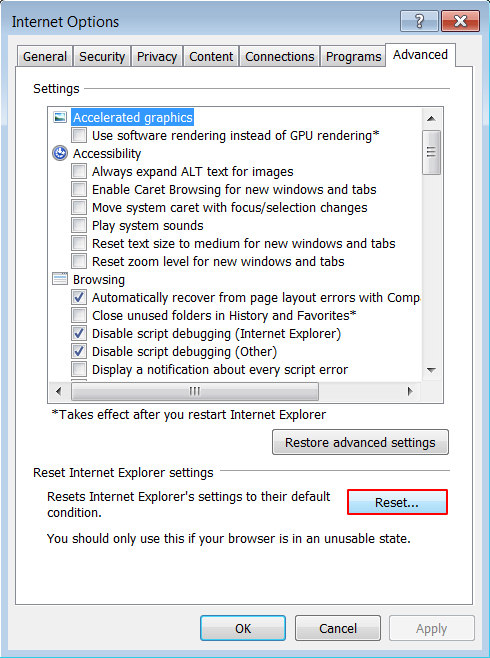
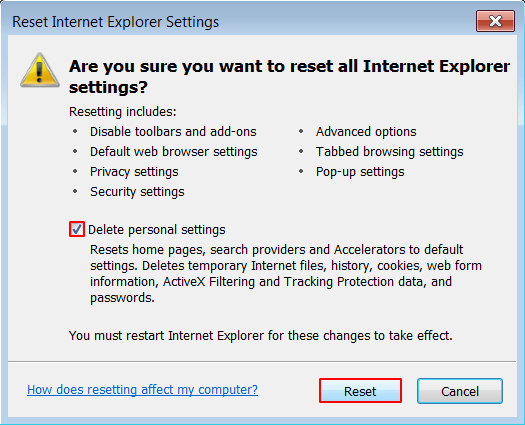
- When IE comes up with the respective screen, read the warning carefully and, if sure, put a checkmark for Delete personal settings. Now click Reset.
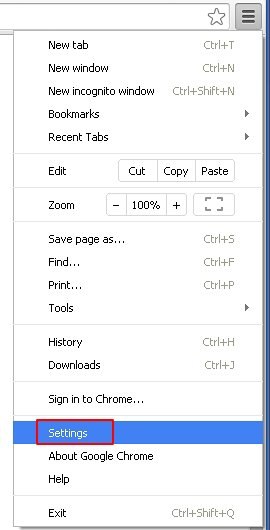
Reset Google Chrome to its default values
- Open your Chrome browser, click the Chrome menu icon to the upper right and select Settings on the list. Alternatively, type in ‘chrome://settings‘ (without quotes) in the URL field.
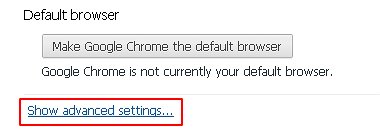
- Find the Show advanced settings… link on the tab that opened up.
- Under Chrome’s advanced settings, click the button that says Reset browser settings.
- Be sure to read the information about the personal settings that will be lost if the transaction gets completed. Click Reset if it’s fine with you.
Complete the TermBlazer removal process
Given the likely persistence of this adware sample, it’s recommended to repeatedly check the machine for its components after the cleanup procedure has been performed. Rescan your system with trusted security suite to make sure TermBlazer extermination has been successful.
Download Ads by TermBlazer free scanner and remover