Learn up-to-date facts about the immensely aggressive CTB Locker ransomware virus and use step-by-step instructions to restore the personal files it encrypted.
While a hardened criminal taking someone hostage is a real-world terror scenario, the activity of the program called CTB Locker is the cyber counterpart thereof. This malicious software has been developed to extort money from people in exchange for the private files it encrypted. This sort of black hat misdemeanor has been going commercial as the respective kit is now sold online for several thousand dollars on hacking forums and similar shady places on the web. In other words, pretty much anyone who has the right sum of money and some distribution resources can get this ransomware up and running to their benefit. The leveraged principles and patterns are not new as there existed similar viruses (CryptoLocker and CryptoWall), but as per investigatory research CTB Locker turns out to be a lot more powerful and technically sophisticated, plus it was most likely designed by a different cyber gang.
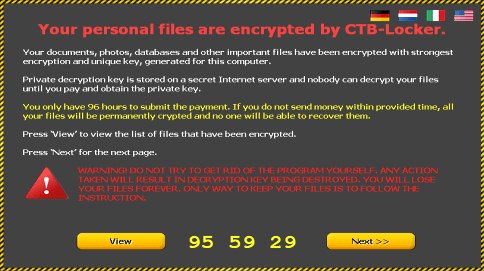
The fraudsters in charge are using exploit kits to deliver the payload to computers, so the contamination is due to outdated software’s vulnerabilities most of the time. As imperceptible as it is, this process gives the ransomware a time advantage before it gets noticed. This span is used for scanning all drives on the computer for the prevalent types of files and encrypting them with elliptic curve cryptography, a very strong algorithm that makes further cracking attempts virtually ineffective. The encrypted chunks of personal information get new extensions, and the original files are erased. It then comes up with a message titled “Your personal files are encrypted by CTB-Locker”, which replaces the victim’s original wallpaper.
According to the alert, the user’s documents, images and other potentially important files have been encrypted, with the decryption key being unique for this PC. The message goes on to say:
“Private decryption key is stored on a secret Internet server and nobody can decrypt your files until you pay and obtain the private key.”
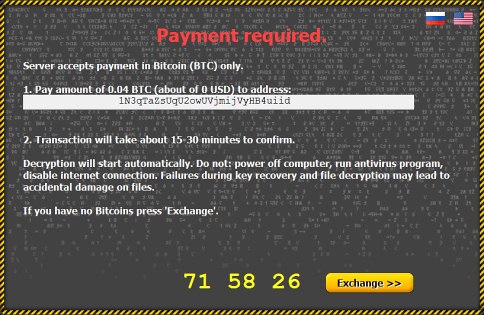
In other words, CTB Locker wants to you pay a sum that equals 0.2 Bitcoin (around 50 USD) before the decryption can commence. The amount may vary, though. In the event the ransom isn’t paid within 96 hours, the data will be irreversibly lost because the private key is going to be no longer available.
For the user to believe that the data isn’t gone, the ransomware offers the feature of restoring up to 5 randomly chosen files. Also, the program has a built-in currency exchange service where you can buy Bitcoins if you have none. An interesting trait of CTB Locker is the fact it communicates with the C&C server through Tor, which makes the connections anonymous. That’s apparently how the bad guys are trying to evade the law enforcement trap. So the victim needs to install Tor Browser Bundle before the payment transactions can even commence.
The bad part about this whole story is you cannot be sure you’ll get your files back intact, unless of course you pay the ransom. There is no tool that can handle the crypto as strong as that for the time being. The good news is there are workarounds that can help you out in recovering the deleted original information or the latest saved versions of your files. So do not hurry with submitting the ransom. Be sure to try the methods described below first.
CTB Locker virus automatic removal
It’s an odd thing but the CTB Locker program itself is not too persistent as far as removal is concerned. Reliable security software does the cleanup job, but be advised this is in no way related to restoring the encrypted data, which is an issue to be touched upon in the next part of this article. So, before you proceed with file restoration, it’s recommended to get rid of the ransomware proper so that it won’t cause you further trouble.
- Download and install the featured security tool and launch an in-depth malware checkup by clicking Start Computer Scan buttonDownload CTB Locker remover
- When the software returns a list of malicious and potentially unsafe items found on the PC, select Fix Threats in order to have the CTB Locker infection uninstalled from your machine. An additional virtue of this process is the elimination of other threats that may be active in the background.
Ways to retrieve personal files encrypted by CTB Locker
Method 1: Backups
Despite the fact that the share of users who regularly back up their data to the cloud or external storage is negligible, they are immune to malware attacks like this. So, if you are lucky enough to be one of these people, use backups to recover your personal information. Before doing so, make sure CTB Locker has been removed from the system (see section above).
Method 2: Data recovery software
According to the recent research, this ransomware encrypts copies of files it detected on a computer. The original documents, photos etc. get erased. This is where you can benefit from file recovery tools which are designed specifically to find and restore objects that were previously removed from a PC. Even though CTB Locker deletes the original files with a number of overwrite passes, utilities like ParetoLogic Data Recovery Pro might address this problem.
Download data recovery software
Method 3: Shadow Volume Copies
There is a feature that Microsoft Windows is shipped with – it’s called Shadow Volume Copies. It means that all files on the computer are automatically subject to copying and storing. Be advised this only applies to the cases where the System Restore feature is turned on; luckily, that’s not a rare scenario. While the newest build of CTB Locker has some built-in countermeasures for recovering Shadow Volume Copies in the regular way, it’s strongly advised to give this method a try. It can be done manually or through the aid of a dedicated automatic tool.
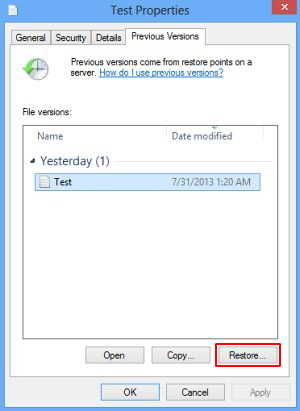
- Recover previous versions of filesPrevious versions are copies of files and folders that are automatically saved by the operating system when a restore point is created. Hopefully changes to your most critical files were made before the latest system restore point – in this case the information in them is going to be accurate for your needs. So do not fail to try this workaround. What you need to do is right-click on a file or folder of interest, select Properties and hit the Previous Versions tab. Then click Restore if you want to file recovered to its previous location, or hit Copy to restore it to a new place.
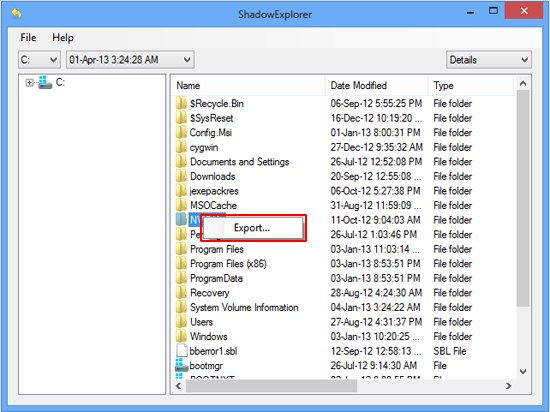
- Use the Shadow Explorer utilityRestoring files and folders can as well be performed automatically. For this purpose, tools like Shadow Explorer can be used. It provides you with all necessary controls and options to restore Shadow Volume Copies within one interface. Just right-click on the file or folder whose copies are to be restored, select Export, and follow the prompts.
Complete the CTB Locker virus removal process
Given the possible tenacity of this ransomware, it’s recommended to repeatedly check the machine for its components after the cleanup procedure has been performed. Now that you have hopefully managed to recover your most important personal files, rescan your system with trusted security suite to make sure CTB Locker extermination has been successful.
Download CTB Locker free scanner and remover


34 comments
Skip to comment form
I cant my files after remove ctb locker .
all my file in this form .jpg , .xlsx , .docx , .rar , .accdb in partition (d)
please help me >
thank you
How to Decrypt files CTB Locker if System Restore was’nt activated…???
Author
Adang, try using data recovery software. Unfortunately, Shadow Volume Copies won’t be available if System Restore hadn’t been active before CTB Locker contaminated the system.
Before I got this virus, I had system restore, had used it in the past. It was removed from my computer by the virus. System restore was empty. Have since cleaned and reformated my computer (thanks to a son).
Author
Sameh, several applicable workarounds to recover the encrypted files are provided in this post, so be sure to read and follow them.
Thanks for the feedback!
my all file is showing DETAILS.XLSX.htrjvdj and i can not open my all files please help me
all my Microsoft office files, Graphic files and pdf files has an extra extension “.zylkiwd” Please help…
Author
Tausif and Dave,
Try the file recovery options and CTB Locker removal tips described in the post.
Hello, my files was locket by CTB-locker. I don,t have previous version ot documents. How i can see it again.Please help. thanks
Author
Tatiana,
Try data recovery software (Method 2 above).
Thank you!
We are data recovery experts. we have been successful in recovering raw data by shadow disk technology.Raw data means files as excel1…excel2…. excel3. these are files that do not have original file names.
Condition: shadow must not be infected. Old cases of infection do not give working data .So one has limited time of about 6 days to recover data in raw format.We have to use data recovery hardware tools to work on imaged copy of the infected source.
Author
Nice tip. Although there actually are quite a few conditions to be met, recovery tools are something that’s definitely worth a try in ransomware scenarios.
I was a victim of the CTB-Locker virus last Friday and said I had 96 hours to pay them. I acted on it quickly and had a computer virus remover agent remove the virus and try to get my files back that were encrypted. Did not have any luck. I paid this computer virus remover $100 USD. However he did install professional version of Microsoft 2010 on my computer and also installed a virus protector so this does not happen again. However, I still do not have any of my files decrypted from the TCB-Locker virus. Does anyone have any suggestions on how to get these encrypted files back. Really the only files I would want back are my pictures of my twins when they were born and every year leading to their age now of 6? I would really appreciate any help or feedback to help me out. This virus is a deadly virus. I do not recall backing up my files:(
Thank you!
Bobby
Author
Bobby, sorry to read about your predicament, some files are precious indeed. We recommend you try the data recovery software, it might be able to pull out the pics that the virus deleted before encrypting their copies. Also, try Shadow Explorer and see if it can locate any previous versions of the files.
My Laptop was effected with CTB locker and i have clean the virus from my system but after that my all file extension is showing:- filename.XLSX.vnxuuem, File name.PDF.vnxuuem and file name.DOCX.vnxuuemExcel,
Now Word, excel and PDF file is not opening.
Author
Vikash, the virus does actually modify the extensions of all files it encrypted. Be sure to try the workarounds listed in the post, in particular, Shadow Copies and the recovery tool. Thanks
All files in my computer has been suffixed with filename.doc followed by “kzowrrj” i.e. filename.doc.kzowrrj due to which files are not opening. Can anyonly please help me. Thanks
Author
Mike, that’s part of the CTB Locker ransomware effect – the encrypted data objects are displayed with random strings following the format name. Successfully restoring your files might be a matter of using data recovery software and / or methods based on Shadow Copies. These recovery vectors are provided in the guide. Hopefully this helps you out.
dear all,,,
plz help me my pc personal file are locked by CTB loker,,,,All ready i remove CTB Locker,,,
But I can’t Open my personal file Such as,, doc,xls, jpg etc,,,,all file ext..are changed ,,,new ext. are detils.xls.kvkbjmn
any one plz help me…..
Author
Didar, try launching the recovery tool linked to above, or run Shadow Explorer app to look for previous versions of the files that could be restored.
How to Decrypt files CTB Locker if System Restore was’nt activated…???
all ms word file this code APXIRPB File how to solve help me?
Author
In case System Restore hadn’t been active prior to CTB Locker attack, no previous versions of your files are available, so the Shadow Volume Copies path won’t work. More likely than not, your last resort is the data recovery method described above. Have you been keeping any backups on external server, etc.?
my all file is showing DETAILS.DWG.klpaohj and i can not open my all files please help me
Author
Alok, this is the typical ransomware routine – all personal files get encrypted and also get new, odd-looking file extensions like the one you mentioned. Please consider trying one of the three options provided in the knowledgebase above. Thanks
I am wondering if paying the ransom will work. Can anyone who has tried this (preferably a reputable business) comment? Would it matter if the virus were removed first?
Author
Submitting the ransom reportedly works, but that’s all at one’s own risk. Before paying, though, all applicable workarounds should be given a shot. If you remove the virus, the ransom payment transaction is no longer an option.
Hello!
I am not infected, and I’d like to avoid it, so I’ve got an important question if anybody can help me:
I’ve got a couple of external hard disks which are connected to a desktop pc. I do not use this pc for anything else except for sharing these harddrives on the local network. These shared folders are given only READ rights across the network, so in theory nobody who is connected to the local network is able to delete or otherwise modify them in any way. These sharing options are set on the host pc as an Administrator.
My question is: if i connect to the local network with another computer (laptop or another pc) and this becomes infected with Ctb-locker, and the files are encrypted, IS THERE ANY CHANCE THAT THE INFECTION CAN ENCRYPT THE FILES IN THE SHARED FOLDERS ? In theory this doesn’t seem possible because the pc which hosts the external HDDs can only be ‘Read’ by the infected computer and not modified in any way.
Please if someone can give a helpful anwer, I’d appreciate it greatly! Thanks
Author
CTB Locker does encrypt data on network shares as long as those are mapped as separate letters. But in your case (no write access), this shouldn’t happen.
Bom galera, na verdade o filho da puta do v?rus, renomeu todos os arquivos. por exemplo contrato.doc.wertyu
vc deve renomea-lo para contrato.doc. s? que fazer isto de todos os arquivos d? muito trabalho
when ctb locker virus i reinstall windows now can i recover files.
Author
We’re afraid the non system files, including ones on HDD volumes other than the system drive, will remain encrypted after Windows is reinstalled, so follow the steps listed in this guide to try and recover the data.
Does not seem to be a way to remove the CTB re-encoded data files or photos. Renaming does not seem to work. What we need is a decoding software for the extensions. Unfortunately I did not back up my data files. So I may lose them. For every lock there is a key just need a clever programmer who knows how to make a decoding program.
Author
Morgan, you are right – renaming files is to no avail. Follow the instructions listed, should help restore encrypted stuff.
NB: Note that the CTB locker virus uses the user credentials to create schedules tasks on the workstation the user logs onto but ALSO on terminal servers (or Citrix) that is triggered by next logon of this user.
So be sure to always check all servers and especially the terminal servers for traces (tasks, executables) of the CTB locker virus or you’ll have the encryption sh*t all over again when the user logs on again.