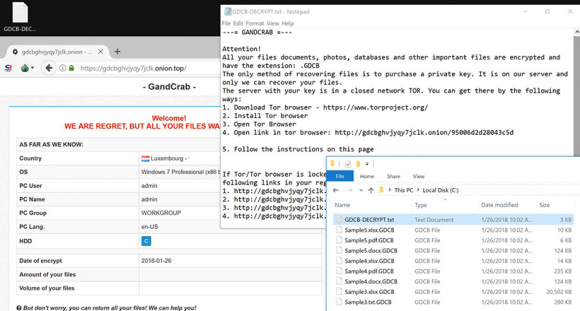
Numerous files with the .GDCB extension on a PC is the way the new GandCrab ransomware signals its presence, so learn how to fix the problem if that’s the case.
It looks like there’s a new high-profile player on the crypto ransomware arena, or an old stager with some groundbreaking tactics up their sleeve. Indeed, there hasn’t been much game-changing stuff going on in this threat landscape lately, but the author of the GandCrab ransomware has managed to add some new hues to it. One of the reasons why this strain is offbeat is because it forces victims to pay in cryptocurrency other than Bitcoin or Monero. Also, it leverages the .bit top-level domain to interact with its C2 infrastructure, which is a trait never seen with ransomware before. And certainly the worst news for the victims is that the .GDCB file virus implements the cryptographic data processing job seamlessly, therefore decryption of the ransomed items is extremely challenging.
GandCrab makers have reportedly built a RaaS (Ransomware-as-a-Service) network around their offending code. What this means is multiple different groups of cybercriminals can join the ‘affiliate’ platform and spread the turnkey ransom Trojan independently while sharing a cut of all ransoms with the devs. This fact explains why there are several concurrent distributions campaigns underway. One of these waves engages the GrandSoft and RIG exploit kits to deposit the culprit on Windows computers. This method harnesses a myriad of compromised websites as well as known vulnerabilities in one’s software, allowing the bad code to trespass without the site visitors’ awareness. Another technique circles around phishing, where users receive emails with fake PDF receipts on board. Once opened, the attached document invokes a number of commands to download a Word file with malicious macros and run a toxic PowerShell script.
Either way, the infection slithers its way into a system undetected and gets down to the extortion part of its mission. It scans the hard drive for files with specific extensions that correspond to the most popular data formats. Then, it utilizes the RSA cryptosystem to lock these files down. To label every such entry, GandCrab appends the above-mentioned .GDCB extension to the original filenames. An inalienable attribute of any ransomware attack is the onset of a ransom note on the target PC, which in this case is GDCB-DECRYPT.txt file. This manual tells the victim to visit one of the crooks’ Tor gateways resolving the GandCrab Decryptor page. That’s where the attackers convey their demands. According to that page, data decryption boils down to submitting a ransom of 1.54 Dash, which is worth about 1200 USD. It is not recommended to surrender to the villains and cough up the cryptocurrency right off. Instead, stick with the walkthrough below to see if the files can be restored by alternative means.
GDCB file virus automatic removal
It’s an odd thing but the GandCrab perpetrating program itself is not too persistent as far as removal is concerned. Reliable security software does the cleanup job, but be advised this is in no way related to restoring the encrypted data, which is an issue to be touched upon in the next part of this article. So, before you proceed with file restoration, it’s recommended to get rid of the ransomware proper so that it won’t cause you further trouble.
- Download and install the featured security tool and launch an in-depth malware checkup by clicking Start Computer Scan buttonDownload .GDCB files virus remover
- When the software returns a list of malicious and potentially unsafe items found on the PC, select Fix Threats in order to have the GDCB file infection uninstalled from your machine. An additional virtue of this process is the elimination of other threats that may be active in the background.
Ways to retrieve .GDCB files encrypted by GandCrab ransomware
Method 1: Backups
Despite the fact that the share of users who regularly back up their data to the cloud or external storage is negligible, they are immune to malware attacks like this. So, if you are lucky enough to be one of these people, use backups to recover your personal information. Before doing so, make sure GandCrab has been removed from the system (see section above).
Method 2: Data recovery software
According to the recent research, this ransomware encrypts copies of files it detected on a computer. The original documents, photos etc. get erased. This is where you can benefit from file recovery tools which are designed specifically to find and restore objects that were previously removed from a PC. Even though the GDCB file virus deletes the original files with a number of overwrite passes, utilities like ParetoLogic Data Recovery Pro might address this problem.
Download data recovery software
Method 3: Shadow Volume Copies
There is a feature that Microsoft Windows is shipped with – it’s called Shadow Volume Copies. It means that all files on the computer are automatically subject to copying and storing. Be advised this only applies to the cases where the System Restore feature is turned on; luckily, that’s not a rare scenario. While GandCrab may incorporate built-in countermeasures for recovering Shadow Volume Copies in the regular way, it’s strongly advised to give this method a try. It can be done manually or through the aid of a dedicated automatic tool.
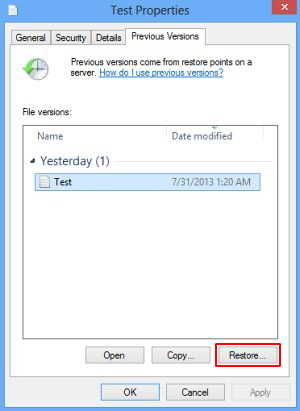
- Recover previous versions of filesPrevious versions are copies of files and folders that are automatically saved by the operating system when a restore point is created. Hopefully changes to your most critical files were made before the latest system restore point – in this case the information in them is going to be accurate for your needs. So do not fail to try this workaround. What you need to do is right-click on a file or folder of interest, select Properties and hit the Previous Versions tab. Then click Restore if you want to file recovered to its previous location, or hit Copy to restore it to a new place.
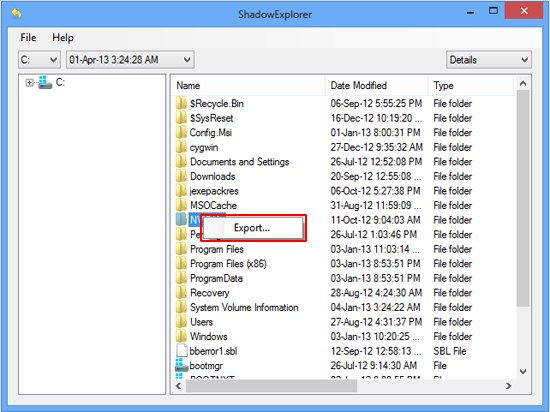
- Use the Shadow Explorer utilityRestoring files and folders can as well be performed automatically. For this purpose, tools like Shadow Explorer can be used. It provides you with all necessary controls and options to restore Shadow Volume Copies within one interface. Just right-click on the file or folder whose copies are to be restored, select Export, and follow the prompts.
Complete the GDCB file virus removal process
Given the possible tenacity of this ransomware, it’s recommended to repeatedly check the machine for its components after the cleanup procedure has been performed. Now that you have hopefully managed to recover your most important personal files, rescan your system with trusted security suite to make sure GandCrab extermination has been successful.
Download GandCrab free scanner and remover