Crypt0L0cker, a recent update to the nasty ransomware that encrypts one’s files, is dissected in this post so that the infected users can resolve their issue.
The latest variant of ransomware, which inherited a name assonant with that of the now defunct CryptoLocker virus, has got a handful of features that do damage to users’ personal information. In fact, in the course of the so-called Operation Tovar held in summer 2014 several agencies took down the Gameover ZeuS botnet, which had been involved in spreading the original malware mentioned above. As it turned out, though, the joy was premature. A number of clones of the malware started to appear a few months later, one of which was TorrentLocker. The ransomware program to be analyzed in the present entry is believed to be a successor of said clone that goes by the name of Crypt0L0cker.
The prevalent attack vector used by this nasty infection is spear phishing. A malicious mass mailing service sends fake emails to potential victims, pretending to be some sort of government notifications or salary-related reports from an employer. Enclosed in these messages are files that look like ZIP attachments which, once opened, trigger a contamination routine that gets deployed in the background.
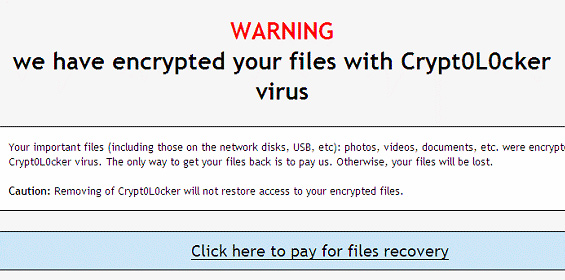
As soon as the destructive code ends up on the computer, it establishes an inconspicuous connection with the criminals-run C&C server, with some initial data exchange on the details of the compromised system taking place behind the scenes. Crypt0L0cker then deploys the scanning phase of its job, trying to find as many personal files as possible. All volumes of the hard drive denoted by a separate letter undergo this impact, moreover any sort of removable media is subject to this processing as well. As a result, objects detected according to the extension-based criterion get encrypted in the blink of an eye and become inaccessible. Every folder containing personal data gets appended by a file with instructions for recovery. The alert that the infected users will encounter says: “Warning! We have encrypted your files with Crypt0L0cker virus.”
The infection claims to be able to provide the decrypt service but it expects a ransom payment in return. The amount of Bitcoins to be submitted ranges from $400-500 (USD equivalent). If the payment deadline of 96 hours expires, the ransom will increase. That’s a lot of money to pay for the things that inherently belong to the victim. In the meanwhile, no computer tech expert can possibly brute-force the decryption key at this time, so it may seem that the situation is hopeless. However, unlike its ill-famed prototype, Crypt0L0cker might reportedly fail to erase the Shadow Copies of encrypted files, so there’s light at the end of the tunnel and the personal information is likely to be recovered through the methods reviewed below. Removal of the ransomware proper is also a must otherwise it will keep messing with your files.
Crypt0L0cker virus automatic removal
It’s an odd thing but the Crypt0L0cker program itself is not too persistent as far as removal is concerned. Reliable security software does the cleanup job, but be advised this is in no way related to restoring the encrypted data, which is an issue to be touched upon in the next part of this article. So, before you proceed with file restoration, it’s recommended to get rid of the ransomware proper so that it won’t cause you further trouble.
- Download and install the featured security tool and launch an in-depth malware checkup by clicking Start Computer Scan buttonDownload Crypt0L0cker remover
- When the software returns a list of malicious and potentially unsafe items found on the PC, select Fix Threats in order to have the Crypt0L0cker infection uninstalled from your machine. An additional virtue of this process is the elimination of other threats that may be active in the background.
Ways to retrieve personal files encrypted by Crypt0L0cker
Method 1: Backups
Despite the fact that the share of users who regularly back up their data to the cloud or external storage is negligible, they are immune to malware attacks like this. So, if you are lucky enough to be one of these people, use backups to recover your personal information. Before doing so, make sure Crypt0L0cker has been removed from the system (see section above).
Method 2: Data recovery software
According to the recent research, this ransomware encrypts copies of files it detected on a computer. The original documents, photos etc. get erased. This is where you can benefit from file recovery tools which are designed specifically to find and restore objects that were previously removed from a PC. Even though Crypt0L0cker deletes the original files with a number of overwrite passes, utilities like ParetoLogic Data Recovery Pro might address this problem.
Download data recovery software
Method 3: Shadow Volume Copies
There is a feature that Microsoft Windows is shipped with – it’s called Shadow Volume Copies. It means that all files on the computer are automatically subject to copying and storing. Be advised this only applies to the cases where the System Restore feature is turned on; luckily, that’s not a rare scenario. While the newest build of Crypt0L0cker has some built-in countermeasures for recovering Shadow Volume Copies in the regular way, it’s strongly advised to give this method a try. It can be done manually or through the aid of a dedicated automatic tool.
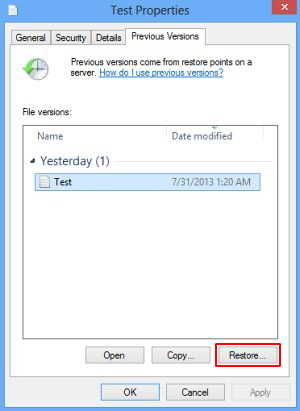
- Recover previous versions of filesPrevious versions are copies of files and folders that are automatically saved by the operating system when a restore point is created. Hopefully changes to your most critical files were made before the latest system restore point – in this case the information in them is going to be accurate for your needs. So do not fail to try this workaround. What you need to do is right-click on a file or folder of interest, select Properties and hit the Previous Versions tab. Then click Restore if you want to file recovered to its previous location, or hit Copy to restore it to a new place.
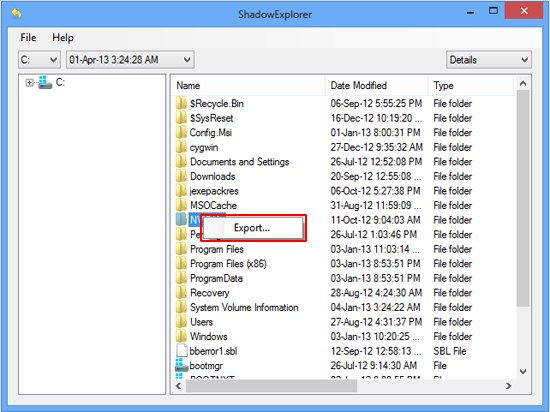
- Use the Shadow Explorer utilityRestoring files and folders can as well be performed automatically. For this purpose, tools like Shadow Explorer can be used. It provides you with all necessary controls and options to restore Shadow Volume Copies within one interface. Just right-click on the file or folder whose copies are to be restored, select Export, and follow the prompts.
Complete the Crypt0L0cker virus removal process
Given the possible tenacity of this ransomware, it’s recommended to repeatedly check the machine for its components after the cleanup procedure has been performed. Now that you have hopefully managed to recover your most important personal files, rescan your system with trusted security suite to make sure Crypt0L0cker extermination has been successful.
Download Crypt0L0cker free scanner and remover