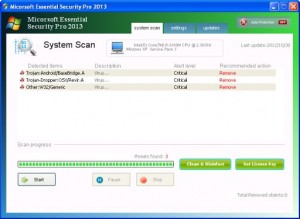
Rogue using name Micorsoft Essential Security Pro 2013
This fake Antivirus comes down from fake flash Update scam sites and immediately runs from where it is dropped to. It doesn’t show fake alerts but it does hijack the .exe file associations in the registry.
Rogue made a transmission to site used for the payment page:
john.denebasendtoend(DOT)pro/users/?ch=1&id=75ab7c06-9dc6-4bbf-b5b9-72b7511a12c3
Registry of file associations hijacking
HKEY_USERS\S-1-5-21-484763869-1844823847-839522115-1003_Classes\.exe
HKEY_USERS\S-1-5-21-484763869-1844823847-839522115-1003_Classes\.exe\DefaultIcon
HKEY_USERS\S-1-5-21-484763869-1844823847-839522115-1003_Classes\.exe\shell
HKEY_USERS\S-1-5-21-484763869-1844823847-839522115-1003_Classes\.exe\shell\open
HKEY_USERS\S-1-5-21-484763869-1844823847-839522115-1003_Classes\.exe\shell\open\command
HKEY_USERS\S-1-5-21-484763869-1844823847-839522115-1003_Classes\.exe\shell\runas
HKEY_USERS\S-1-5-21-484763869-1844823847-839522115-1003_Classes\.exe\shell\runas\command
HKEY_USERS\S-1-5-21-484763869-1844823847-839522115-1003_Classes\exefile
HKEY_USERS\S-1-5-21-484763869-1844823847-839522115-1003_Classes\exefile\DefaultIcon
HKEY_USERS\S-1-5-21-484763869-1844823847-839522115-1003_Classes\exefile\shell
HKEY_USERS\S-1-5-21-484763869-1844823847-839522115-1003_Classes\exefile\shell\open
HKEY_USERS\S-1-5-21-484763869-1844823847-839522115-1003_Classes\exefile\shell\open\command
HKEY_USERS\S-1-5-21-484763869-1844823847-839522115-1003_Classes\exefile\shell\runas
HKEY_USERS\S-1-5-21-484763869-1844823847-839522115-1003_Classes\exefile\shell\runas\command
HKEY_CURRENT_USER\Software\Classes\.exe
HKEY_CURRENT_USER\Software\Classes\.exe\DefaultIcon
HKEY_CURRENT_USER\Software\Classes\.exe\shell
HKEY_CURRENT_USER\Software\Classes\.exe\shell\open
HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command
HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas
HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command
HKEY_CURRENT_USER\Software\Classes\exefile
HKEY_CURRENT_USER\Software\Classes\exefile\DefaultIcon
HKEY_CURRENT_USER\Software\Classes\exefile\shell
HKEY_CURRENT_USER\Software\Classes\exefile\shell\open
HKEY_CURRENT_USER\Software\Classes\exefile\shell\open\command
HKEY_CURRENT_USER\Software\Classes\exefile\shell\runas
HKEY_CURRENT_USER\Software\Classes\exefile\shell\runas\command
HKEY_CLASSES_ROOT\.exe\DefaultIcon
HKEY_CLASSES_ROOT\.exe\shell
HKEY_CLASSES_ROOT\.exe\shell\open
HKEY_CLASSES_ROOT\.exe\shell\open\command
HKEY_CLASSES_ROOT\.exe\shell\runas
HKEY_CLASSES_ROOT\.exe\shell\runas\command
The rogue can be removed with manually, however, because of file associations Hijacking and possible infections by other malware that may have been included, it is best to use our Antivirus removal tool, VIPRE Antivirus.
You can download a free trial of Vipre to remove the rogue by clicking on the link below:
http://www.vipreantivirus.com/Antivirus-Trial/VIPRE-Antivirus/
If you are unable to download and install our malware removal tool because the rogue has infected your computer and is not allowing you to install the program, you can use our VIPRE Rescue Disc here: