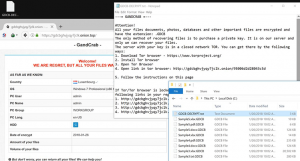
Numerous files with the .GDCB extension on a PC is the way the new GandCrab ransomware signals its presence, so learn how to fix the problem if that’s the case. It looks like there’s a new high-profile player on the crypto ransomware arena, or an old stager with some groundbreaking tactics up their sleeve. Indeed, …
Category: Ransomware
Oct 10
Remove hairullah@inbox.lv ransomware virus and recover encrypted files
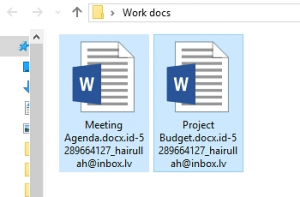
In case file extensions on a computer have been appended with hairullah@inbox.lv, it indicates a ransomware issue that must be fixed as soon as possible. Samples of a new ransom Trojan are being continuously reported by users who happened to fall victim to another vicious extortion attack. The attribute that all infestation encounters have in …
Jul 17
Remove CryptoWall ransomware and decrypt abducted files in Windows
The impact caused by CryptoWall virus, which encrypts one’s data and holds it hostage while extorting a ransom, can be reversed using these instructions. The malicious software to be dissected in this entry was once believed to have gone extinct, but the disappointment and fuss about it came back as its version 3.0 emerged back …
May 15
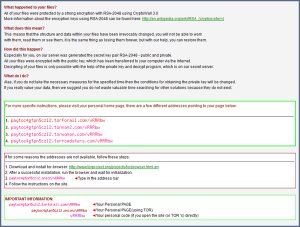
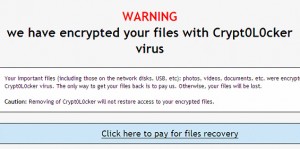
Remove Crypt0L0cker virus ransomware and recover encrypted files
Crypt0L0cker, a recent update to the nasty ransomware that encrypts one’s files, is dissected in this post so that the infected users can resolve their issue. The latest variant of ransomware, which inherited a name assonant with that of the now defunct CryptoLocker virus, has got a handful of features that do damage to users’ …
Feb 06
Remove CTB Locker ransomware and recover encrypted personal files
Learn up-to-date facts about the immensely aggressive CTB Locker ransomware virus and use step-by-step instructions to restore the personal files it encrypted. While a hardened criminal taking someone hostage is a real-world terror scenario, the activity of the program called CTB Locker is the cyber counterpart thereof. This malicious software has been developed to extort …