DNS Unlocker app inundates one’s browser with excessive ads under the guise of providing web traffic filtering features, so get rid of this adware right away. There is a fine line between legit and adware backed ecommerce. What is more, the average user may find it hard to tell the difference with the naked eye. …
Aug 17
Virtual machine service – High CPU and memory usage process
The macOS operating system features a process named com.apple.Virtualization.VirtualMachine, responsible for managing virtualization tasks. This process is crucial for the operation of various applications that depend on virtualization, such as Docker. However, in certain scenarios, this process might consume excessive CPU and RAM, resulting in performance degradation. The issue with Docker on macOS A significant …
Mar 25
How to remove Yahoo redirect virus from Mac
Get the lowdown on the Yahoo redirect virus Mac problem to learn how the virus spreads, what damage it causes, and how to remove it from an infected computer. Back in the day, when Mac malware was the exception rather than the rule, it was hard to believe that it could reach the heights seen …
Mar 09
Remove Easy Calendar virus from Chrome, Firefox and IE
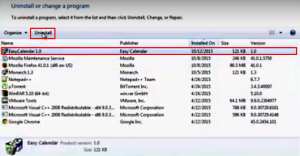
Easy Calendar seems to be an innocuous application for organizing tasks and adding reminders, but it acts as an adware and hence doesn’t belong on a computer. It may appear that no particular hazard should ever emanate from simplistic and lightweight apps like calendars, at least the inherently harmless idea underlying these sorts of programs …
Oct 12
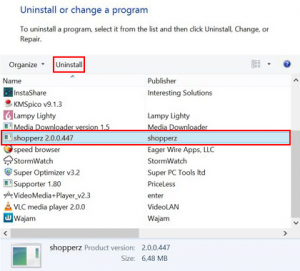
Uninstall Shopperz adware from Firefox, Chrome and IE
Remove Shopperz app and get its ads out of the browser by leveraging a technique which ensures thorough and hassle-free cleanup of this adware junk. Collecting and redeeming points for the routine web browsing activity is a game the Shopperz app tries to get its customers involved into. It all ends up being not that …
Feb 22
GDCB file virus: GandCrab decryptor and removal
Numerous files with the .GDCB extension on a PC is the way the new GandCrab ransomware signals its presence, so learn how to fix the problem if that’s the case. It looks like there’s a new high-profile player on the crypto ransomware arena, or an old stager with some groundbreaking tactics up their sleeve. Indeed, …
Oct 10
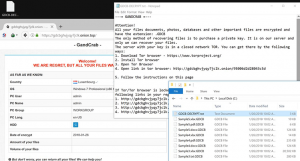
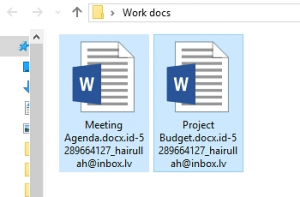
Remove hairullah@inbox.lv ransomware virus and recover encrypted files
In case file extensions on a computer have been appended with hairullah@inbox.lv, it indicates a ransomware issue that must be fixed as soon as possible. Samples of a new ransom Trojan are being continuously reported by users who happened to fall victim to another vicious extortion attack. The attribute that all infestation encounters have in …
Oct 01
Remove Sonic Train ads from Firefox, Chrome and IE
Since the Sonic Train software renders users’ web browsing insufferable and endangers their privacy, removal of this adware shouldn’t be dallied off. Not so many Internet surfers would willingly opt into expanding the volume of advertising they see online. Ads are everywhere anyway, some people would argue, but it’s redundancy that makes the principal difference. …
Oct 01
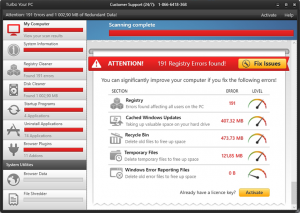
Remove Turbo Your PC (TurboYourPC) malware
Although Turbo Your PC software is distributed in a fancy wrapping of purportedly efficient system optimization, it is a rogue and should thus be uninstalled. Computer health does not go hand in hand with Turbo Your PC application, despite the fact that the publisher of this product is trying to convince people these concepts are …
Sep 27
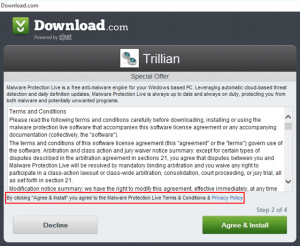
Uninstall Malware Protection Live (MalwareProtectionClient.exe) virus
Malware Protection Live app is delivered via freeware setup clients without users’ approval, so it obviously does not belong on a PC and should be removed. Software installation, regretfully, isn’t always preceded by and based on the computer user’s consent, though it certainly should be. This attribute constitutes a pretty unequivocal delineation between what’s regular …
Sep 25
Remove Gangnam Game popup virus (gangnamgame.net) from Chrome, Firefox and IE
The commonplace adware elimination tactics are inefficient for handling Gangnam Game popup virus, so follow these steps to get the whole security job done. The malicious specimen to be dissected in this post is built more intricately than the overwhelming majority of adware threats. Run-of-the-mill samples of browser operation disrupting code tend to center around …